Modern web browsers have grown into creatures resembling, to a large extent, the very operating systems they run on. Yes, I’m looking at you, Chrome/ium. I haven’t done any serious research on it, but I’d wager that almost all the people using desktops or laptops have a browser open in the background at any given time. As a consequence of their nature and footprint, browsers have more exposed attack surfaces than any other regular application. Yet when you look at what they are driven by, it’s mostly content outside your control! Unless you’re submitting forms all day, the vast majority of requests initiated by your browser will be in response to external stimuli.
Of course designers and programmers go to great lengths to mitigate those dangers, but a paranoid type such as myself never likes to bestow safety so easily into the hands of others. Back in the days of using Windows as my primary operating system, I loved the feature of ZoneAlarm firewall which let you decide whether or not an executable could access the Internet. For a very long time it’s been bugging me that I couldn’t conveniently see and influence where my browser sends data. Thus, I was excited to discover that a similar concept had been implemented for Chrome and Firefox.
Enter the (u)Matrix
I stumbled upon uMatrix a couple of months ago. Unsuprisingly, it has been occupying the first place in my personal ranking of Firefox extensions ever since.
It has evolved from http-switchboard, which split into uBlock Origin and uMatrix itself. While uBlock focuses on pre-defined list of requests to block, its cousin acts like a configurable firewall, preventing the browser from making certain types of requests in various contexts - visited domains. Let’s say you visit your favourite blog, which loads some JavaScript off facebook.com. With uMatrix you can block exactly those requests without affecting content fetched from other domains.
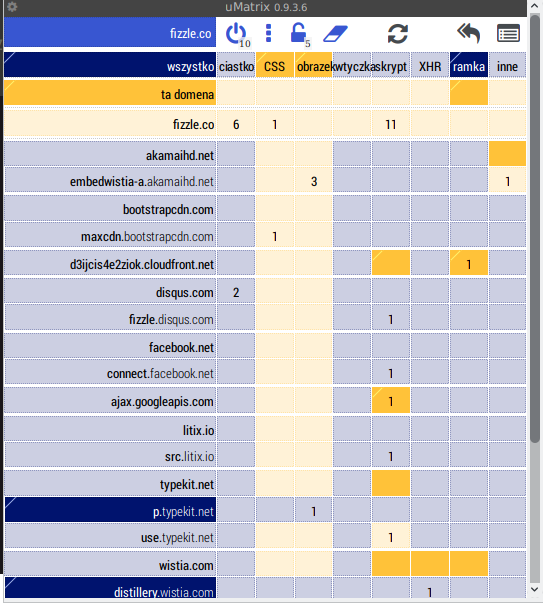
uMatrix dashboard
By default, there are no restrictions on loading anything from the domain you’re visiting and its subdomains. All the other domains, however, are restricted to only serve images and CSS. The extension comes with several lists of known malicious and tracking domains, where nothing is fetched from. It goes without saying that everything is configurable and in fact pretty soon after uMatrix is first enabled you discover that it breaks the Internet.
With great power comes great responsibility
Isn’t it empowering to finally know all the places your browser is calling when you visit your favourites? Frankly, I never knew many of the blocked tracking domains existed. Some of them pop up in the dashboard regularly. That said, before you jump straight in and install uMatrix in your dad’s browser, let’s take a look at the immediate repercussions of doing so.

Most places on the Web these days are better described by the word application than website. Media-rich content and large quantities of JavaScript abound. Unfortunately, that means that the experience of browsing those sites is going to be severely affected with default settings of uMatrix. The effects range from disappearing or misaligned menus to completely broken apps like Google Docs to you being greeted with a blank page. Yep, there are sites out there that just won’t load at all without 3rd party JavaScript. Graceful degradation, anyone?
Usually once you’ve loaded a page and glanced at the dashboard it’s obvious what needs to be allowed to load. More often than not, however, loading of one scripts causes a request to yet another (sub-)domain, so it may take up to six “allow-reload” cycles until you get the page fully working. In most cases, once the main page is okay you need to allow a couple more cells until the login area/form is functional, if the site has one.
Bending the rules
Naturally, the initial ‘learning’ phase depends on how many websites you visit most often. For me, after a week of regular browsing and adjusting the matrix I was able to come back to pre-filtering level of comfort. That is, with the added peace of mind that all the AdWords and Facebook tracking code is no longer following me everywhere I go.
I realise that a week of clicking around and mashing F5 just to browse like you should might be too much. Therefore I want to share with you my curated rules file that you can import straight into uMatrix. It contains a minimal set of rules necessary for the following web apps sans tracking at the time of writing:
- Buffer overlay browser extension on all domains
- airbnb.co.uk
- asciiflow.com
- atlassian.com
- bitbucket.org
- bitly.com
- buffer.com
- coursera.org
- digitalocean.com
- docsend.com
- entrepreneur.com
- evenbrite.co.uk
- facebook.com
- forbes.com
- google.co.uk, google.com
- heroku.com
- jsfiddle.net
- linkedin.com
- meetup.com
- msdn.com
- paypal.com
- player.vimeo.com (embedded videos)
- quora.com
- skype.com
- skyscanner.net
- slack.com
- slideshare.net
- stackoverflow.com
- trello.com
- twitter.com
- typeform.com
- yelp.co.uk
- youtube.com
Fetching scripts from code.jquery.com and ajax.googleapis.com is allowed for all domains.
Furthermore, it enables referrer spoofing and User-Agent spoofing for every domain. It makes it harder to fingerprint your browser and doesn’t break any of the sites I visit on a regular basis.
Grab the rules, import them in uMatrix control panel, don’t foget to commit so they become permanent and Bob’s your uncle! You’ve now got a foundation to build upon.
I hope this helps making your online identity less exposed, even if just by a tad. I’m waiting to hear about your experience of uMatrix!